2025Hgame- Week2 - WriteUp
赛后碎碎念
第一次参加Hgame,感觉非常不错,难度适中,能做出题)而且还完成了人生中第一次一血成就,实属非常高兴,只可惜一些太难的题实在是没琢磨出来怎么做(说的就是lost disks,做了好几天没研究出来Luks怎么解密),最后的排名应该在130多位,只做了misc和一题web一题crypto的情况有这个排名已经很满意了,比不上全栈大佬哈哈哈,希望以后能再接再厉吧qwq
misc
Invest in hints
知识点省流
本题考查人性&脑洞
WP
先来看看题目信息——无舍即无得,然后给了25个提示,每个提示都有一串长度为71的01字符串,每个提示都对应了真正提示的一个字符串,并且字符串的个位代表原串的第一个字符(可以用14点数解锁一条提示,共25条,加起来共350分,正好是题目的分数),同时题目也说明了不需要暴力枚举。
根据得到的信息,一开始的思路是二进制转ascii得到字符串,但转换后得到的都是乱码,随后各种方法,包括但不限于:位移,求余,异或,进制转换,各种可疑编码加密……都解不出来
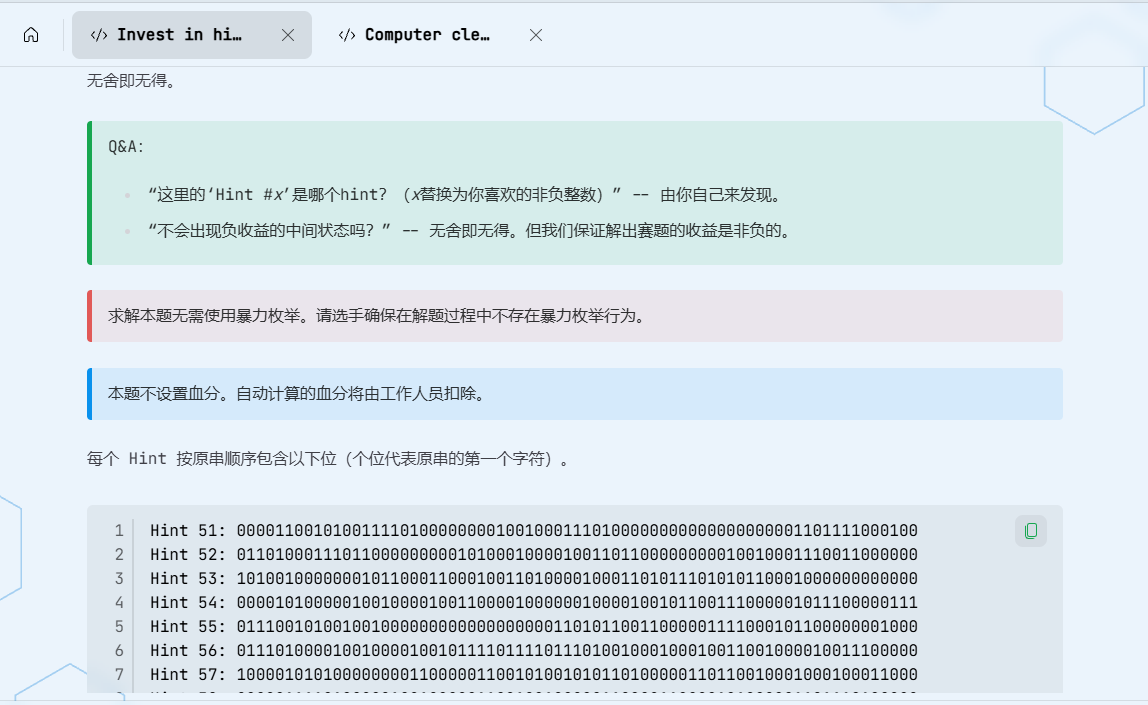
实在没辙,遂解锁了一个提示看看怎么个事,刚开始没看出什么关系,后面又多解锁了几个提示(反应的还是慢了,浪费了一些分数),慢慢想明白了解题思路
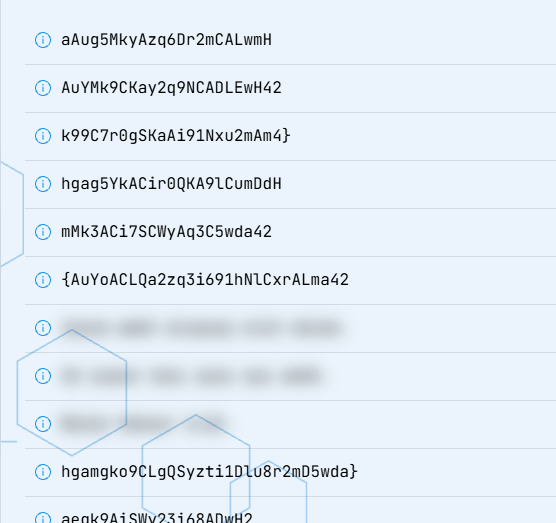
以第四条提示为例,他的01字符串和原串对应如下:
00001010000010010000100110000100000010000100101100111000001011100000111
hgag5YkACir0QKA9lCumDdH
显然根据比赛的情况,flag的开头为hgame,所以这个字符串开头的三个字符是正确的,而01字符串的最后三位正好为1(还记得字符串的个位代表原串的第一个字符吗),在这个基础上,解锁了几条hint后,我发现hint字符串的长度与01字符串中1的数量是对应的,依旧以第四条提示举例,其01字符串中有23个1,而原字符串则正好是23位长度,恰恰说明了他们的对应关系——大胆猜测,flag的长度是71位,对应了71位长度的01字符串,当对应位置的值为1时,则表达为对应位置的flag的字符,当对应位置的值为0时,则不表达,举个例子↓
假设flag为 hgame{123}
则对应的01字符串为 1111111111
那 0000011111
对应的则是 hgame
0101010101
对应 hae13
1010101010
对应 gm{2}
第四条提示的01字符串翻转后,直观对应如下
11100000111010000011100110100100001000000100001100100001001000001010000
hga g5Y k ACi r0 Q K A 9 lC u m D d H
确定了对应关系后,开始解题:显然这不是一个编码加密类题目,所以凭空想象是解不出来的,解锁hint是必然步骤(也正如题目invest in hints,只不过挑选合适的hint解锁可以省很多点数),然后根据解锁的hint去拼出正确的flag即可
下面是我的拼凑方法(这里将01字符串翻转了,符合我们的阅读习惯)
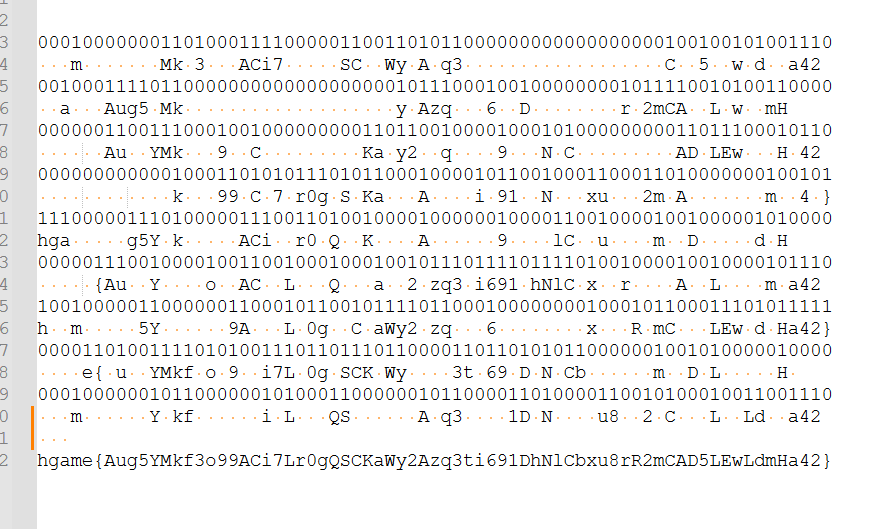
为什么说考验人性,因为前面卡住没有进展的原因就是因为觉得不解锁hint的情况下也能解出题目(就是说想多贪点分数),做完才发现越贪越做不出来,实际上并不是什么难的题目,可能就是因为这个所以解题数也不多吧)
Computer cleaner plus
知识点省流
本题考查linux取证分析
WP
根据题目信息,我们要在虚拟机里找到可执行恶意文件,一开始的想法是用find找一下exe和sh文件,但没什么效果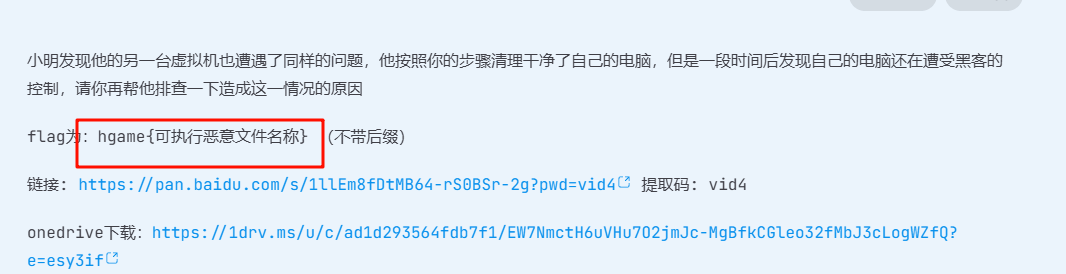
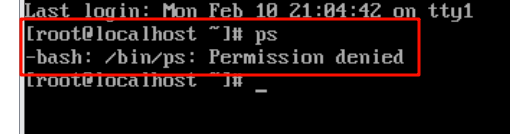
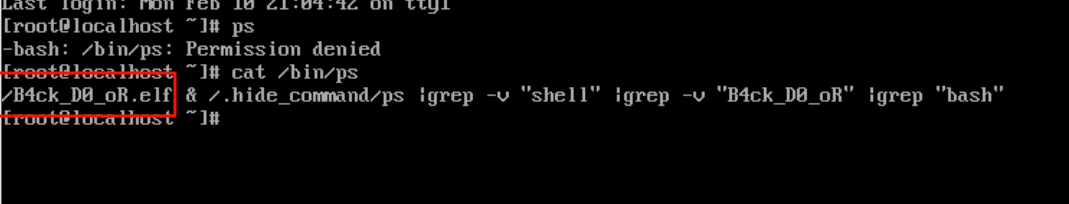
然后根据题目说电脑被黑客控制,考虑到这个恶意文件会不会在运行中,所以想到看看有什么进程在运行,执行ps的时候发现显示无权访问,非常的奇怪,所以就查看了一下ps的内容,然后发现ps被恶意修改了,里面就有我们需要找的恶意文件名称
Level 729 易画行 (一血)
知识点省流
本题考查区块链(sepolia)
WP
下载附件得到一个ts文件,简单用大模型分析了一下,这是个typescript脚本,大概就是转移交易了一个NFT,发送地址是0x74520Ad628600F7Cc9613345aee7afC0E06EFd84
根据给出的地址,我们可以去Sepolia Etherscan这个链接查询具体的交易详情,进去搜索给出的地址,因为根据代码是进行NFT交易,所以我们查看NFT Transfers,然后可以看到这个NFT id很眼熟啊)

点击这个NFT看看其交易详情,发现有两条记录,都看看
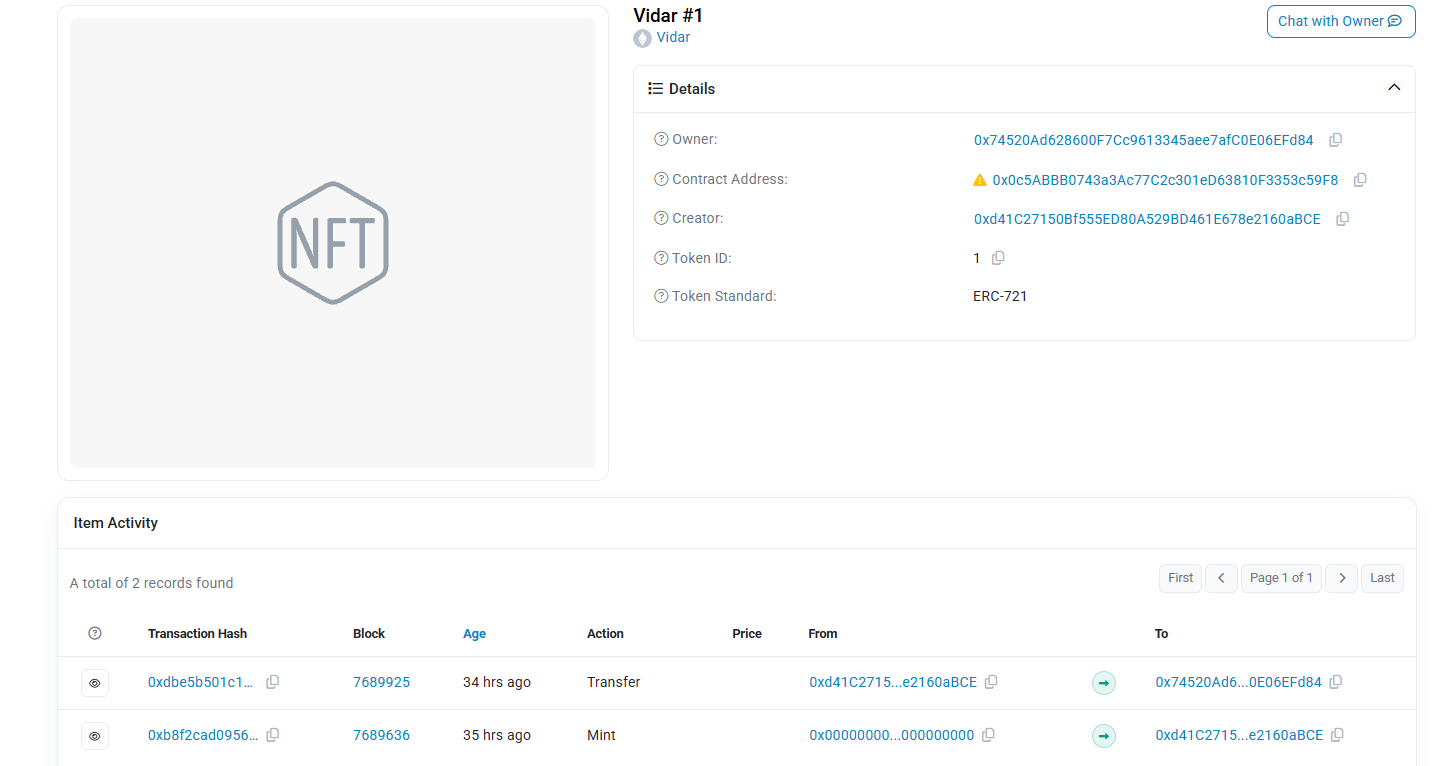
发现在第二条记录的详情中,将数据解码后,有一条ipfs链接,简单了解一下访问姿势,除了下载ipfs客户端外,也可以通过web端的方法访问——https://ipfs.io/ipfs/QmUusCYT8GTNgbDk5WAHZsHmHSxqcxuHov94inyFcpPqM6
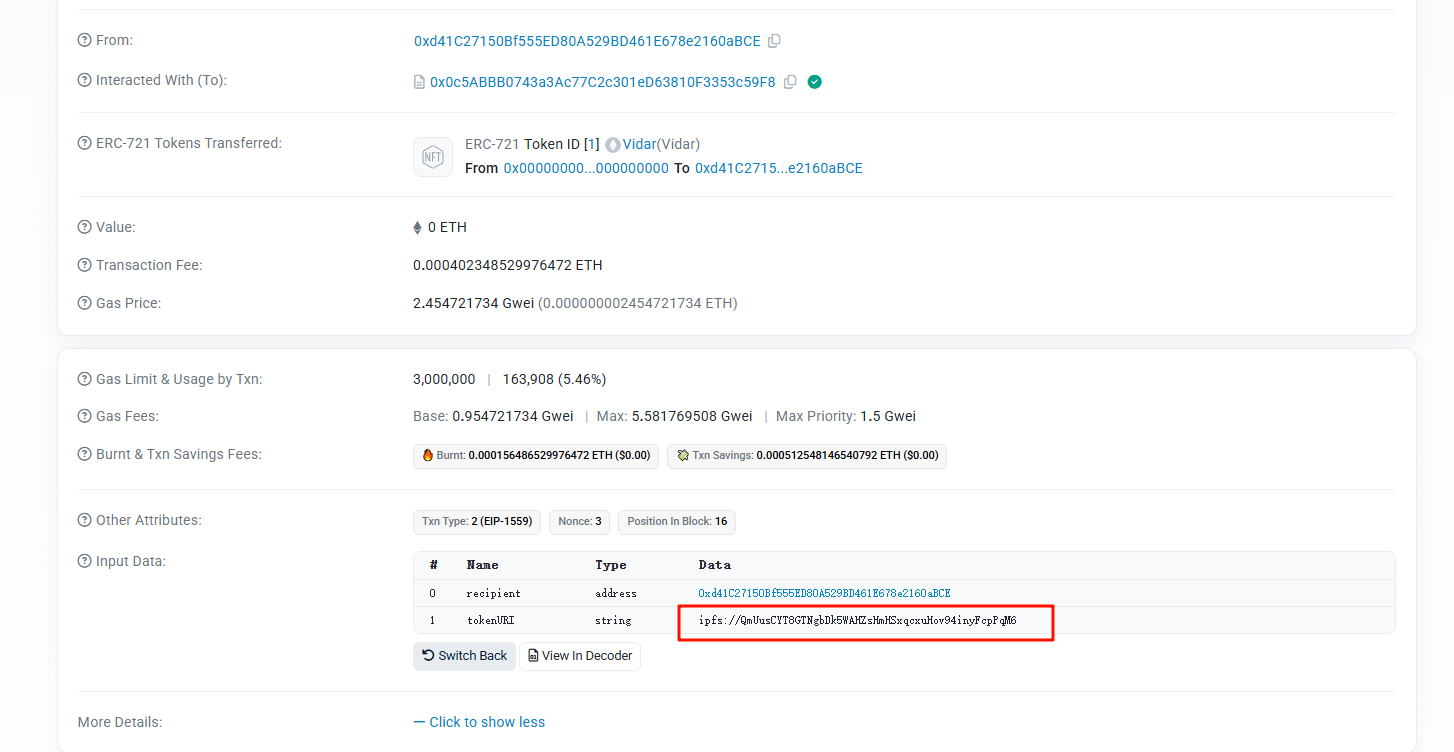
进去后即可发现flag
纪念一下自己的第一次一血)
Crypto
Ancient Recall
知识点省流
本题考查我也不懂 ds梭哈
WP
将py文件丢给ds梭哈即可
Major_Arcana = ["The Fool", "The Magician", "The High Priestess","The Empress", "The Emperor", "The Hierophant","The Lovers", "The Chariot", "Strength","The Hermit", "Wheel of Fortune", "Justice","The Hanged Man", "Death", "Temperance","The Devil", "The Tower", "The Star","The Moon", "The Sun", "Judgement","The World"]
wands = ["Ace of Wands", "Two of Wands", "Three of Wands", "Four of Wands", "Five of Wands", "Six of Wands", "Seven of Wands", "Eight of Wands", "Nine of Wands", "Ten of Wands", "Page of Wands", "Knight of Wands", "Queen of Wands", "King of Wands"]
cups = ["Ace of Cups", "Two of Cups", "Three of Cups", "Four of Cups", "Five of Cups", "Six of Cups", "Seven of Cups", "Eight of Cups", "Nine of Cups", "Ten of Cups", "Page of Cups", "Knight of Cups", "Queen of Cups", "King of Cups"]
swords = ["Ace of Swords", "Two of Swords", "Three of Swords", "Four of Swords", "Five of Swords", "Six of Swords", "Seven of Swords", "Eight of Swords", "Nine of Swords", "Ten of Swords", "Page of Swords", "Knight of Swords", "Queen of Swords", "King of Swords"]
pentacles = ["Ace of Pentacles", "Two of Pentacles", "Three of Pentacles", "Four of Pentacles", "Five of Pentacles", "Six of Pentacles", "Seven of Pentacles", "Eight of Pentacles", "Nine of Pentacles", "Ten of Pentacles", "Page of Pentacles", "Knight of Pentacles", "Queen of Pentacles", "King of Pentacles"]
Minor_Arcana = wands + cups + swords + pentacles
tarot = Major_Arcana + Minor_Arcana
def reverse_fortune_wheel(FATEd):
sum_FATEd = sum(FATEd)
sum_FATE = sum_FATEd // 2
FATE0 = (FATEd[4] - FATEd[3] + FATEd[2] - FATEd[1] + FATEd[0]) // 2
FATE1 = FATEd[0] - FATE0
FATE2 = FATEd[1] - FATE1
FATE3 = FATEd[2] - FATE2
FATE4 = FATEd[3] - FATE3
assert FATE4 + FATE0 == FATEd[4], "Reverse error"
return [FATE0, FATE1, FATE2, FATE3, FATE4]
# 给定的最终Value列表
final_value = [
2532951952066291774890498369114195917240794704918210520571067085311474675019,
2532951952066291774890327666074100357898023013105443178881294700381509795270,
2532951952066291774890554459287276604903130315859258544173068376967072335730,
2532951952066291774890865328241532885391510162611534514014409174284299139015,
2532951952066291774890830662608134156017946376309989934175833913921142609334
]
# 逆向250次操作
current_value = final_value.copy()
for _ in range(250):
current_value = reverse_fortune_wheel(current_value)
# 生成初始牌名
cards = []
for v in current_value:
if v < 0:
index = v ^ (-1)
if 0 <= index < len(Major_Arcana):
card = Major_Arcana[index]
cards.append(f"re-{card}")
else:
card = tarot[v]
if card in Major_Arcana:
cards.append(card)
else:
cards.append(card)
# 生成flag
flag = "hgame{" + "&".join(cards).replace(" ", "_") + "}"
print(flag)



